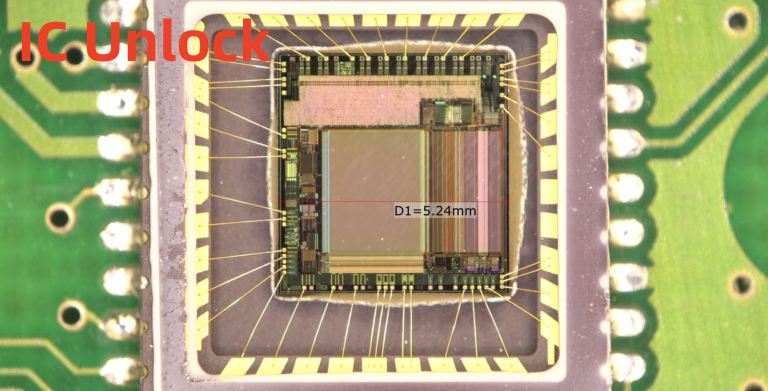
IC unlock is also called IC decryption, IC attack, or IC crack. Normally, a final product’s IC is encrypted. Services for IC unlock is mainly to decrypt an IC using semiconductor reverse engineering methods. After IC unlock services, a programmer would be able to read the ICs programs.
Let us consider the different approaches for IC unlock.
Approaches for IC Unlock
In this section, we will be considering the different approaches used for unlocking an IC. Let’s begin
Software Attacking
This technology attacks ICs making use of the communication interfaces of the processor and then exploits security holes, cryptographic algorithms, and protocols present in these algorithms. One example of this attack is the attack made on the earlier ATMEL AT89 microcontroller family.
This attacker capitalized on loopholes present in the erasing operation’s timing design of different microcontrollers. It achieved this by utilizing a program that was self-designed, putting a stop to the next phase of erasing the memory data of the program, after erasing the locking bit of the encryption. This program now became non-encrypted and then the programmer only read out its on-chip program.
Furthermore, using encryption methods for attacking ICs is possible with the development of newly-created attacking devices, using some software to perform software attacks. Recently, China has an attacking device called Kai Ke Di decryption equipment. This was developed by a professional in IC attacking from the Chengdu area of China. The device can perform IC unlock majorly through SyncMos.Winbond, as a result of loopholes present in the process of IC production.
The method involves the utilization of some programmers in locating inserted bytes to discover if the chip comes with a continuous slot. These inserted bytes can perform instructions that would end the internal program and then make use of a decryption device for decrypting and obtaining the program.
Electronic Detection Attacking
Typically, this technology helps in monitoring the analog characteristic of the processor of all interface and power connections all through the normal operation with a high temporal attack and resolution through the monitoring of the characteristics of the electromagnetic radiation. Due to the fact that the microcontroller serves as an actively functioning electronic device, there is a change in the corresponding consumption of power as its performs the different instructions.
With this, the attacker will be able to get some critical information concerning the microcontroller through the analysis and detection of these changes making use of mathematical statistics and special instruments for electronic measurement.
The RF programmer on the other hand will be able to read the encryption MCU program’s old model to utilize this principle.
Error Generation Attacking Technology
This technology makes use of operating conditions that are abnormal for causing processor errors. Then the processor offers more access for enabling the attacks. Also, clock strikes and voltage are the most widely used technologies for error generation.
High-voltage and low-voltage attacks are useful for disabling the protection offered to the circuit as well as force processors to perform wrong operations. The clock transition might reset a protection circuitry without having to disrupt your protected information. Clock and power transitions could alter the execution and decoding of one instruction in several processors.
Probe Technology
This technology helps to directly expose the internal connections of the chop and then checks, manipulates, and interferes with a microcontroller so as to successfully achieve the attack’s purpose.
UV Attacking
UV attacking involves the application of ultraviolet radiation on chips, as well as converting an encrypted chip to one that is non-encrypted and then makes use of a programmer in reading the program. The method is okay for the OTP chips, as well as engineers whose designing microcontrollers understand that you can only erase the OTP chips using ultraviolet light. Therefore, in order to clear the encryption, you must make use of UV.
Presently, majority OTP chips manufactured in Taiwan could be decrypted making use of this method. 50% of the OTP chips ceramic packages would have a quartz window. Also, this IC type could be irradiated directly with UV light. If the package is in plastic form, there is a need to first open this chip, you can expose the wafer to UV light.
Due to the relatively poor chip encryption, the main decryption doesn’t require costs. This is why the chip’s market price is extremely cheap.
Chip loopholes
Majority of chips feature cryptographic vulnerabilities at the design time. These types of chips have the ability to exploit vulnerabilities in the chip to attack them and then read the code present in the memory. Also, if you can locate the FF code which could be inserted bytes, then reversing the program out could be possible.
Furthermore, if the search code features a specific byte, then you can make use of the byte for reversing out the program. Chips like Shimao or Winbond MCU chips, for example, the W78E516 decryption, AT89C51 decryption, is to utilize the code’s byte loopholes to attack.
Also, there are some loopholes which are present inside the chip, like the pin inside the encryption would become the non-encrypted chips, when including an electronic signal. Due to the fact that this attacking technology deals with a MCU Chinese manufacturer, these models would not be listed here. The devices for chip decryption which could be seen on the market these days would make use of the loopholes present in the program or chip to achieve IC unlock. Moreover, the methods or approaches, which could be shared, will only be able to unlock a few models, since their attacking approaches are very confidential to the companies or labs.
In our company, we have been able to create our own specialized equipment mainly for internal use. Also, we possess the technology as well as reliable tools that can help achieve IC unlock. For example, MS9S09AW32, as well as devices which can unlock the LPC2119LPC2368 specifically, as well as other related ARM ICs. These outcomes would be extremely reliable by making use of specific approaches and tools designed for the IC catalog.
The FIB Recovery Encryption Method
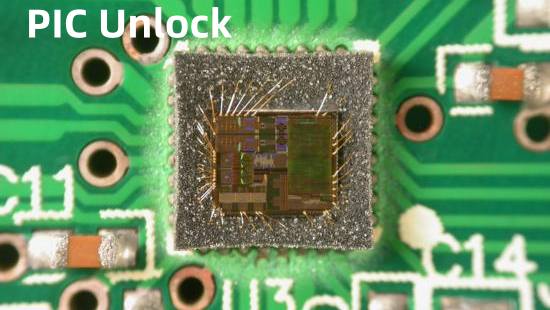
The FIB recovery encryption method is appropriate for a good number of chips having fuse encryption. The MSP430 unlocking of TI is a typical example. Because this MSP430 encryption helps in burning the fuse, so far you can restore the fuse, and then the IC can change to the non-encrypted chips. Other models like MSP430F1101A, MSP430F425, MSP430F149, etc.
Normally, we make use of the probe in achieving the reconnection of the fuse. When there’s no equipment, then you can still achieve this through the modification of the lines that contracts to the companies offering semiconductor modification. Generally, it could make use of the focused ion beam (FIM) equipment in connecting the lines, or by using the equipment’s laser modification in order to restore the line.
However, this method isn’t the preferred solution. This is because there is always a need for consumables and equipment which usually increases the cost of the customers for all IC unlock related works. This technology will be utilized when there is no better option or method.
Modification of Encryption Circuits
Presently on the marketplace, DSP and CPLD chip designs are usually complex, with a high encryption form of performance; making use of the method above is through decryption.
Also, we will have to make the initial analysis mentioned for the structure of the chip, and then locate the encryption circuits, and then make use of the chip circuits modifying equipment for making some changes, as well as making the failure of the encryption circuits.
The encrypted CPLD or DSP then would be into the non-encrypted status that the code will be able to read out.
What IC Unlock Services Do We Offer?
The following are the IC Unlock Services that we provide for our customers.
- Disassembling of the bin files and C programming
- Advanced IC research and testing algorithms
- Supports different IC types including ARM, AVR, PLD, and CPLD
- Secondary development as well as chip program upgrade
- Decrypting of integrated circuits, developing and designing, as well as failure analyzing
- Focused ion beams (FIB), transmission electron microscopy (TEM), as well as scanning electron microscopy (SEM)
- One stop reverse engineering services offered for semiconductors and integrated circuits
- Single-chips microcomputer as well as DSP system development.
Conclusion
In summary, services for IC unlock is mainly to decrypt an IC using semiconductor reverse engineering methods. After IC unlock services, a programmer would be able to read the ICs programs. There are different approaches used for unlocking an IC.
For software attacks, it attacks ICs making use of the communication interfaces of the processor and then exploits security holes, cryptographic algorithms, and protocols present in these algorithms. Error Generation Attacking Technology makes use of operating conditions that are abnormal for causing processor errors. Then the processor offers more access for enabling the attacks.
Also, we have included different IC Unlock Services that we provide for our customers. You can feel free to communicate your requests to us.